AverageSecurityGuy
Security, Programming, Pentesting
Pwning a Splunk Server
by {"login"=>"averagesecurityguy", "email"=>"stephen@averagesecurityguy.info", "display_name"=>"averagesecurityguy", "first_name"=>"", "last_name"=>""}
Update
Marc Wickenden also found this bug a while back and did an excellent write up on it. He also built a metasploit module to exploit the bug.
Splunk has this nifty feature that allows you to upload custom applications that include Python scripts, which are used for custom searching. In Splunk Free this feature becomes a vulnerability because anyone can access the web interface without authenticating. This means you can upload and execute arbitrary code in the context of the Splunk user. If the Splunk user has admin access to the server then the server can be completely compromised.
If you are using Splunk Free, make sure the web server is not running under an administrative account and if possible, configure a web server such as Apache or IIS to sit in front of Splunk and force users to authenticate. Here's an article showing how to do this with Apache.
The Rest of the Story
During a recent pentest I stumbled upon a Splunk server that allowed access to the administrative interface with no authentication. While trying to figure out how to run queries on the server I came across this article. The article says you can create a custom Python script to query data in Splunk. I already had a Python shell script, now I needed to figure out how to create a custom application.
More searching turned up this article and an example application on github. Splunk provides users with an example application called custom_search and in the bin directory you will find a usercount.py file. All I had to do was replace the contents of this file with my Python shell and I had a malicious application.
To create the custom application, use git to clone the splunk-sdk-python repository, then copy the custom_search directory to another location. Replace the contents of usercount.py with your Python script, make sure you inlcude the #! line. Next tar gzip the custom_search folder and use the management interface to upload an application from a file. Once the application is uploaded, you can launch it.
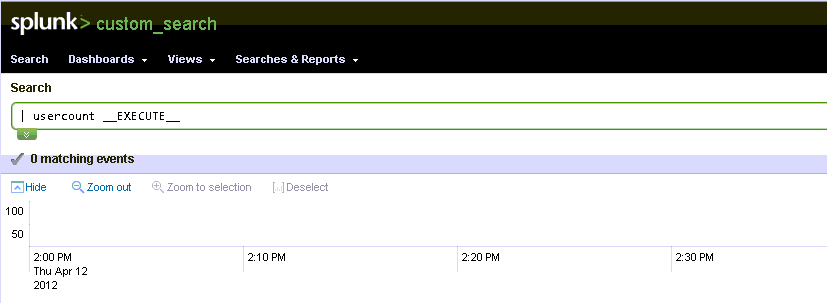
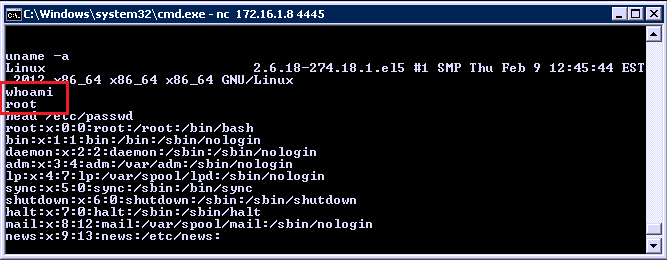
Once the application is running you can execute the custom search using the following command: | usercount __EXECUTE__. When the search executed my shell started and I used netcat to connect to it. This instance of Splunk was running as root, game over.
Side Note
What I don't mention in this article is that it took me a few hours to go from identifying the Splunk server to executing code. I don't use Splunk and I am not familiar with how it works so I stumbled around for a long time and almost gave up number of times. If you are new to pentesting and are struggling, don't give up because your hard work will eventually pay off.
tags: penetration testing - Splunk - Splunk vulnerability