02 Dec 2011
I have started using Inssider from metageek.com to do wireless surveys for clients. I like the program but it doesn't have a method for viewing previously saved GPX log files. I know the files can be converted to KML and displayed in Google Earth or Google Maps but what I wanted was a simple way to parse the file for a list of wireless access points. I couldn't find anything that simple so I wrote a ruby script.
Gpx_view.rb reads a GPX file and outputs the wireless access points identified in the file. The output format can be short or long. The short format prints each wireless access point once while the long format prints each instance of the wireless access point. The default format is short. To format the output, I used the table formatting code from the Rex library in metasploit. I didn't want to install the entire Rex gem, which you can get here, so I copied the file lib/rex/ui/text/table.rb from the gem and made it a standalone module. You can download gpxview.rb and rextable.rb from github.
Here's a sample of the short format:
MAC Address SSID RSSI Channel Encryption Quality
----------- ---- ---- ------- ---------- -------
XX:XX:XX:XX:XX:XX -58 6 WEP 73
XX:XX:XX:XX:XX:XX -49 6 RSNA-CCMP 91
XX:XX:XX:XX:XX:XX -55 6 RSNA-CCMP 91
XX:XX:XX:XX:XX:XX -51 1 RSNA-CCMP 90
XX:XX:XX:XX:XX:XX -53 11 RSNA-CCMP 90
XX:XX:XX:XX:XX:XX -62 11 RSNA-CCMP 88
XX:XX:XX:XX:XX:XX -58 6 RSNA-CCMP 90
XX:XX:XX:XX:XX:XX -51 1 RSNA-CCMP 91
18 Nov 2011
For centuries people learned a trade by becoming an apprentice to a master craftsman. After spending a number of years, typically seven, working under the master they became a journeyman and were able to start their own business. A journeyman was able to become a master only after presenting a "master piece" to his respective guild. Once you became a master, then you were allowed to take on an apprentice and start the process over. If we look at information security as a hands on craft, what would you learn as an apprentice on your way to becoming a journeyman? What would a "master piece" look like?
I think an apprenticeship program would look something like this:
Years 1 and 2 - Networking and System Administration
- Gain a thorough understanding of common network protocols like TCP/IP, Ethernet, ARP, UDP, and ICMP.
- Gain a thorough understanding of DNS, DHCP, Active Directory, SMTP, FTP, and other common network services.
- Gain ability to perform administrative tasks on both Windows and Linux machines.
- Learn to automate common administrative tasks using scripting languages such as bash, perl, python, ruby, vb, and powershell.
Years 3 and 4 - Risk Assessment and Disaster Planning
- Understand the common risks to which your network and systems are exposed.
- Understand how to mitigate those risks.
- Understand how to build redundancy into your network and systems so that a single failure does not take down the entire system.
Years 5 and 6 - Vulnerability Assessment and Exploitation
- Understand common network and system vulnerabilities and how to fix them.
- Understand methods, both automated and manual, of finding vulnerabilities.
- Understand methods, both automated and manual, of exploiting vulnerabilities.
- Understand methods for preventing vulnerabilities in networks, systems and code.
Year 7 - Communication
- Understand how to effectively communicate in written form (ie. documentation and reporting).
- Understand how to effectively communicate in verbal form (ie. presentations, meetings).
- Understand the different "languages" of your audience (ie. IT department, CIO, CEO).
I know there are a lot of details missing from this outline, especially if we are thinking about this as a hands on craft, but I think it is a good place to start. I would like to know what you would add to this outline, particularly what hands on activities would you place under each category. I have a shared Google document here that you can update with your thoughts. I will leave the document open unless people abuse it.
08 Nov 2011
We ask a lot of questions that we don't want answered honestly and we know when not to answer certain questions honestly. If you think about it, how many times do you say "How are you doing?" without expecting an honest answer or waiting to get one? And there is not a man in his right mind that is going to tell a woman "yes" when she asks, "Does this dress make me look fat?" We don't really want honesty, we want people to tell us what we want to hear.
This lack of desire for honesty holds true in the security industry as well. Typically, it plays out like this: a client requests a security assessment, you perform the work and create a report that is an honest assessment of their security posture, the client begs you to modify the report to keep them from looking so bad. A lot of times you give in because you don't want to lose the client. This cycle is the reason companies continue to get plundered by attackers and why we are still dealing with security issues that should have been fixed years ago.
If you are a company seeking a security assessment, fix the problems in the report instead of arguing over the severity rating. If you provide security assessment services don't placate your clients by modifying the report to suit them, find new clients that want honest answers.
"Honesty and transparency make you vulnerable. Be honest and transparent anyway." -- Mother Teresa
10 Oct 2011
I was watching Derbycon videos the other day and saw a great presentation by Chris Gates (@carnal0wnage) and Rob Fuller (@mubix) titled "The Dirty Little Secrets They Didn't Teach You in Pentesting Class." In the presentation they discuss a lot of tips and tricks pentesters can use to improve their pentests. One slide in particular caught my attention:
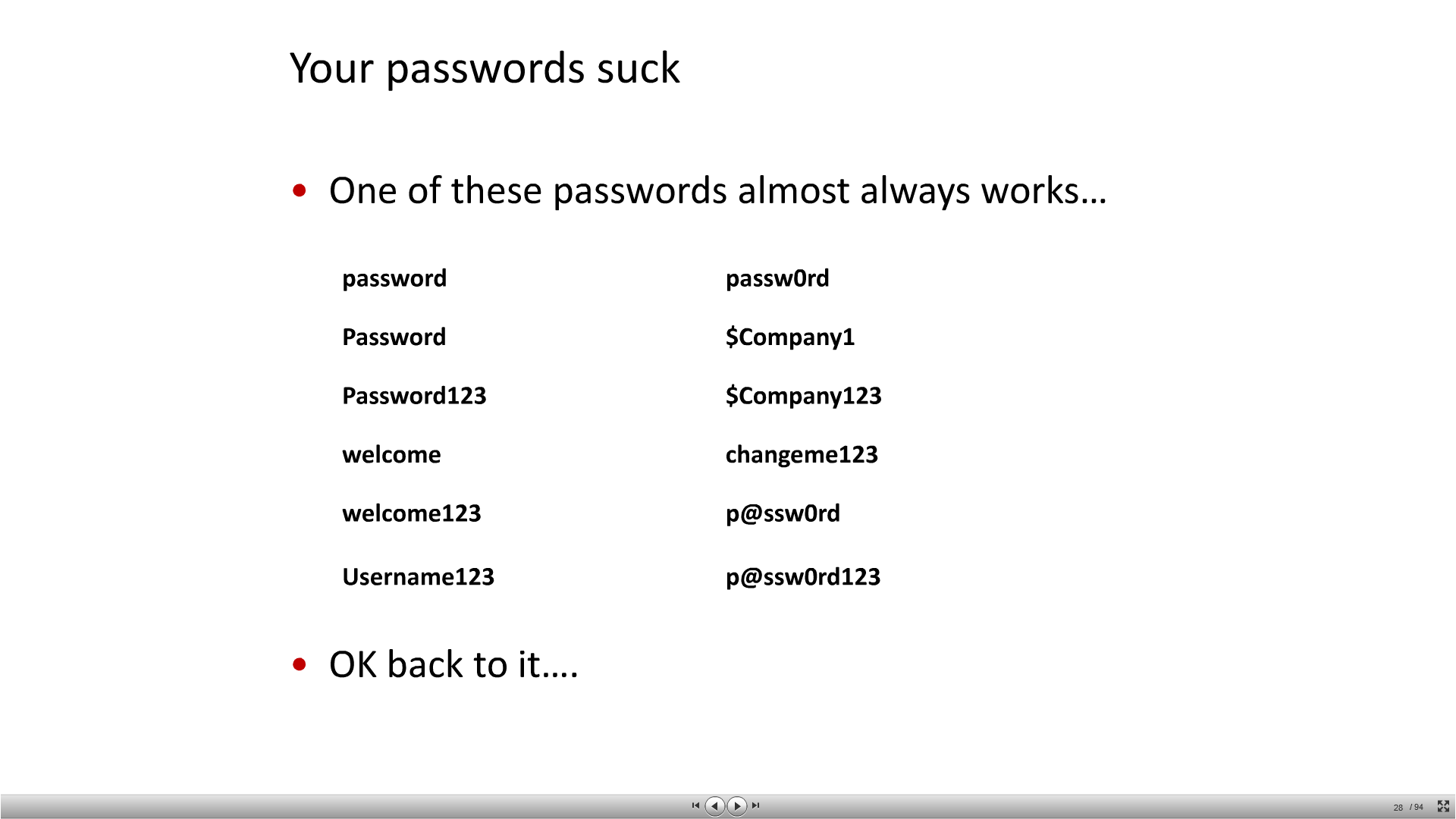
I couldn't help but think, it can't be that easy, but they are much more experienced than I am so I have to trust them. I decided to test this out on my next pentest, so I wrote a quick python script that will take a username or file of usernames and a company name or a file of company names and generate a new file of colon separated username and password combinations, which can be used in most password testing software. You can get the script here.
Using the script is easy, the command weak_passwords.py -u admin -c passco > user_pass_list will create a file called user_pass_list with the following username password combinations.
admin:password
admin:password123
admin:Password
admin:Password123
admin:p@ssw0rd
admin:p@ssw0rd123
admin:P@ssw0rd
admin:P@ssw0rd123
admin:p@ssword
admin:p@ssword123
admin:P@ssword
admin:P@ssword123
admin:passw0rd
admin:passw0rd123
admin:Passw0rd
admin:Passw0rd123
admin:welcome
admin:welcome123
admin:Welcome
admin:Welcome123
admin:welc0me
admin:welc0me123
admin:Welc0me
admin:Welc0me123
admin:changeme
admin:changeme123
admin:Changeme
admin:Changeme123
admin:passco
admin:passco123
admin:Passco
admin:Passco123
admin:admin
admin:admin123
admin:Admin
admin:Admin123
You can then use the list in any password auditing tool that takes a file of colon separated username password combinations, such as hydra, medusa, or metasploit.
10 Oct 2011
Metasploit includes an OpenVAS module, which allow you to interact with an OpenVAS server to create targets, run scans, download reports, and import reports. Recently I had the opportunity to make some updates to the module and wanted to write a blog post to document how to use it. This blog post does not cover how to setup an OpenVAS server but you can find that info here and here. Before I go any further, I need to thank George Birmingham for reporting the bugs in the original code and for helping me test the updates. His comments and suggestions were invaluable.
To use the OpenVAS integration you need to load the openvas module within msfconsole. Do this by running the command load openvas. The updates to the openvas module were accepted in revision 13851, so you may need to use msfupdate to get the updated modules.
After the module is loaded, the workflow is very basic. Start by connecting to the server using the command openvas_connect. If you connect to a host other than localhost or 127.0.0.1, then you will need to pass an additional paramater of "ok" to the command. If you forget the "ok" parameter you will be warned that there is no SSL support and your interaction with the server is not secure. Also, you need to use the port for the OpenVAS manager server, openvasmd, which defaults to 9390.
msf > openvas_connect sbh sbh 127.0.0.1 9390
[*] Connecting to OpenVAS instance at 127.0.0.1:9390 with username sbh...
[+] OpenVAS connection successful
Next, create a target to scan using the command openvas_target_create. If you want spaces in the name or comment then make sure you place quotations around them.
msf > openvas_target_create "Local Machine" 192.168.70.128 "My Local Machine"
[*] OK, resource created: db1175ac-b40b-4b13-9a80-24b68c2c6b40
[+] OpenVAS list of targets
ID Name Hosts Max Hosts In Use Comment
-- ---- ----- --------- ------ -------
0 Localhost localhost 1 1
1 Local Machine 192.168.70.128 1 0 My Local Machine
Next, create a task by specifying a target and a configuration. Use the command openvas_config_list to get a list of configurations and the command openvas_target_list to get a list of targets.
msf > openvas_config_list
[+] OpenVAS list of configs
ID Name
-- ----
0 Full and fast
1 Full and fast ultimate
2 Full and very deep
3 Full and very deep ultimate
4 empty
msf > openvas_task_create "Local Scan" "Scan My Local Machine" 0 1
[*] OK, resource created: 483c6f03-6490-4de2-bd81-c1c5b217d950
[+] OpenVAS list of tasks
ID Name Comment Status Progress
-- ---- ------- ------ --------
0 Local Scan Scan My Local Machine New -1
Next, start the task with openvas_task_start and watch the progress using openvas_task_list.
msf > openvas_task_start 0
[*] OK, request submitted
msf > openvas_task_list
[+] OpenVAS list of tasks
ID Name Comment Status Progress
-- ---- ------- ------ --------
0 Local Scan Scan My Local Machine Running 2
msf > openvas_task_list
[+] OpenVAS list of tasks
ID Name Comment Status Progress
-- ---- ------- ------ --------
0 Local Scan Scan My Local Machine Running 98
msf > openvas_task_list
[+] OpenVAS list of tasks
ID Name Comment Status Progress
-- ---- ------- ------ --------
0 Local Scan Scan My Local Machine Done -1
Once the scan is finished, the progress is -1, list the available reports using openvas_report_list.
msf > openvas_report_list
[+] OpenVAS list of reports
ID Task Name Start Time Stop Time
-- --------- ---------- ---------
0 Example task Tue Aug 25 21:48:25 2009 Tue Aug 25 21:52:16 2009
1 testtask Fri Sep 16 14:21:31 2011 Fri Sep 16 14:23:09 2011
2 Local Scan Fri Oct 7 22:52:46 2011 Fri Oct 7 23:04:48 2011
Next, you can download (openvas_report_dowload) or import (openvas_report_import) the report. You must specify the report format with either command. You can get a list of formats using openvas_format_list. When importing a report you must use the NBE format. Also note, that when trying to download an ITG or PDF report my OpenVAS server returns an empty report, YMMV.
msf > openvas_format_list
[+] OpenVAS list of report formats
ID Name Extension Summary
-- ---- --------- -------
0 CPE csv Common Product Enumeration CSV table.
1 HTML html Single page HTML report.
2 ITG csv German "IT-Grundschutz-Kataloge" report.
3 LaTeX tex LaTeX source file.
4 NBE nbe Legacy OpenVAS report.
5 PDF pdf Portable Document Format report.
6 TXT txt Plain text report.
7 XML xml Raw XML report.
msf > openvas_report_download 2 1 /root/ov/reports
[*] Saving report to /root/ov/reports/report-d76434b0-38e6-462c-87e1-717622056e86.html
msf > openvas_report_import 2 4
[*] Importing report to database.
You can see all the available commands using the command openvas_help. If you have any questions or find any bugs in the openvas module let me know at averagesecurityguy [at] gmail [dot] com so I can fix them. If you want to look at the code, it is in /opt/framework/msf3/plugins/openvas.rb and /opt/framework/msf3/lib/openvas/openvas-omp.rb. Enjoy.
