AverageSecurityGuy
Security, Programming, Pentesting
VMware Security Basics - Part 3
by {"login"=>"averagesecurityguy", "email"=>"stephen@averagesecurityguy.info", "display_name"=>"averagesecurityguy", "first_name"=>"", "last_name"=>""}
This is the final entry of a three part series on VMware Security Basics. Part 1 is here and part 2 is here. The first part describes a typical ESX environment and the minimum considerations for the security of the storage system, the second part describes security considerations for the ESX servers, and this part describes security considerations for the guest operating systems.
As a reminder, a typical ESX environment looks like the diagram below:
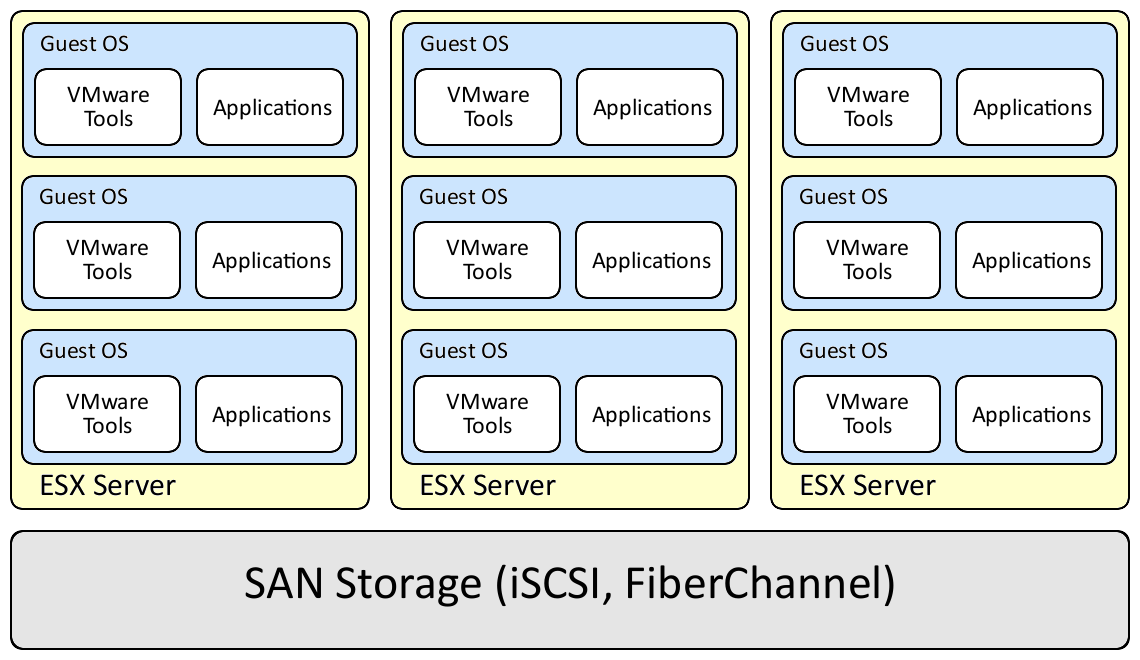
Guest Operating Systems
The thing to remember with guest operating systems is they are just like any other computer on the network and must be secured appropriately.
Secure the Guest OS
Each guest OS should be hardened to match the security context in which it resides and all security updates should be applied. If possible create a hardened template and use the template to deploy new VMs. The template should be updated regularly to apply new security updates. In addition to security updates for the OS, apply security updates for third-party applications as well.
Keep VMware Tools Updated
In most ESX environments, VMware Tools is installed on the guest operating systems. Just like any other software VMware Tools must be updated regularly to apply security updates.
Virtual Machines are Files
Virtual machines are files and can be copied and pasted like any other file. Control who is allowed to move or copy VM files and where VM files can be stored. Backups of virtual machines should be encrypted.
Backup Your Virtual Machines
Having a redundant storage system and replication does not take the place of backups. Virtual machine files can be corrupted like any other files. Replication will give you multiple copies of a corrupted VM, it won't allow you to restore a good copy of the VM.
Watch Out for Dormant VMs
Dormant VMs are machines that have been shutdown and left unused for a while. These machines are typically missing critical security updates and pose a risk to the network when they are brought back online. Virtual machines that are no longer needed should be backed up and removed from production ESX servers. If it is necessary to use a dormant VM, then it should be brought online in a test environment so that security updates can be applied before placing it back into production.
Conclusion
I hope you found this series of blog entries useful for securing your VMware environment. If you want more information please read the resources listed at the beginning of part 1, which is here.
tags: VMware - VMware security