AverageSecurityGuy
Security, Programming, Pentesting
VMware Security Basics
by {"login"=>"averagesecurityguy", "email"=>"stephen@averagesecurityguy.info", "display_name"=>"averagesecurityguy", "first_name"=>"", "last_name"=>""}
Virtualization is complex and there are many moving parts. I can not speak to all the details of hardening a VMware environment but I can speak to the minimum things to consider when installing or maintaining a VMware environment. For more advice, look at these documents:
- vSphere 4.0 Security Hardening Guide
- Security Configuration Benchmarks for VMware ESX 4
- PCI DSS Virtualiztion Guidelines
- A Guide to Virtualization Hardening Guides
A Typical ESX Environment
A typical ESX environment will have one or more ESX servers connected to a shared storage system such as a fiber channel or iSCSI SAN. Each ESX server will have one or more guest operating systems, each with VMware tools and a myriad of applications installed. This can be seen in the figure below:
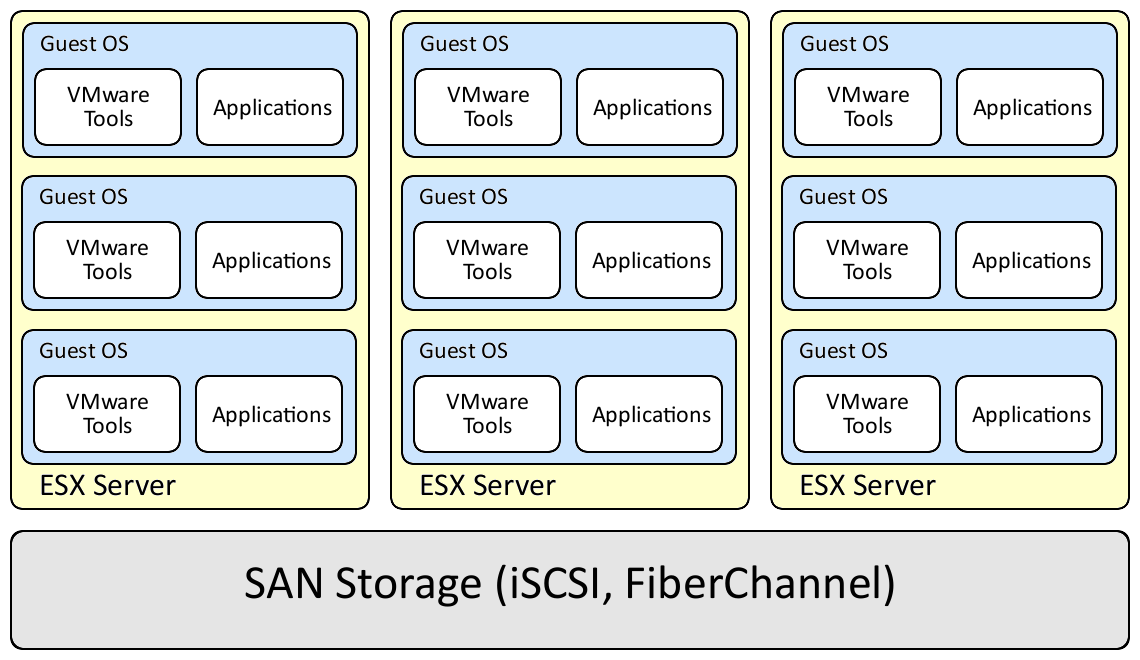
In this environment there are three major areas of concern: the storage system, the ESX servers, and the guest operating systems.
Storage Systems
Four things to think about with storage systems are data availability, traffic isolation, the security levels of the ESX servers sharing the storage systems, and which ESX servers are allowed to see which data sets.
Data Availability
Whatever storage system is used, fiber channel or iSCSI, ensure there are multiple data paths between the storage system and the ESX servers. This includes dual controllers on the SAN, dual switches, redundant power sources for the SAN, and dual host bus adapters (HBA) on the ESX server. It is not enough to have a single HBA with dual ports, two HBAs are necessary. Before the system goes into production, testing should be done to ensure a single device failure does not prevent the ESX server from accessing the data.
Traffic Isolation
Traffic isolation is of particular concern in iSCSI systems because they use the same basic infrastructure as a standard network. All iSCSI traffic should be segmented from the rest of the network traffic to prevent an attacker from sniffing the iSCSI data. I am not a fan of using VLANs to segment traffic of differing security levels and always recommend physically segmenting iSCSI traffic from the rest of the network.
Shared Storage for ESX Servers with Differing Security Levels
ESX servers in differing security levels are configured and maintained differently. An ESX server setup as a lab environment is not going to be hardened to the same level as an ESX server holding the companies production systems and those two ESX servers should not share the same storage. An attacker who gained access to the weaker ESX server could use it to attempt to gain access to the production data on the shared storage system.
Share Data Volumes with the Appropriate ESX Servers
On a typical SAN, multiple data volumes are configured and each one is assigned a SCSI logical unit number (LUN), which is used to uniquely identify that volume. The SAN can then be configured to only allow specific HBAs to access specific LUNs. As an example, in a group of ESX servers only two of those servers may need access to the LUN that holds the HR data, the SAN should be configured so only the HBAs in those ESX servers have access to the LUN with HR data.
Conclusion
As stated earlier there are three major areas of concern with a production VMware environment, the storage system, the ESX servers, and the guest operating systems. I will discuss the latter two in upcoming blog entries. For now, remember to configure and test multiple paths to the data on the storage system, to isolate iSCSI traffic from the rest of the network, to keep ESX servers of differing security levels from sharing the same storage system, and to only share data sets with the appropriate ESX servers.
tags: best practices - VMware - VMware security