AverageSecurityGuy
Security, Programming, Pentesting
Using SET Credential Harvester On a Site With No Login Form
by {"login"=>"averagesecurityguy", "email"=>"stephen@averagesecurityguy.info", "display_name"=>"averagesecurityguy", "first_name"=>"", "last_name"=>""}
I was working on a social engineering engagement recently and wanted to try to gather usernames and passwords from the victims. The Social Engineering Toolkit (SET) has a credential harvesting attack option that is designed specifically for this purpose. There was a small catch, the client's web site did not have a login form. I was able to use some custom HTML and CSS to get around this issue.
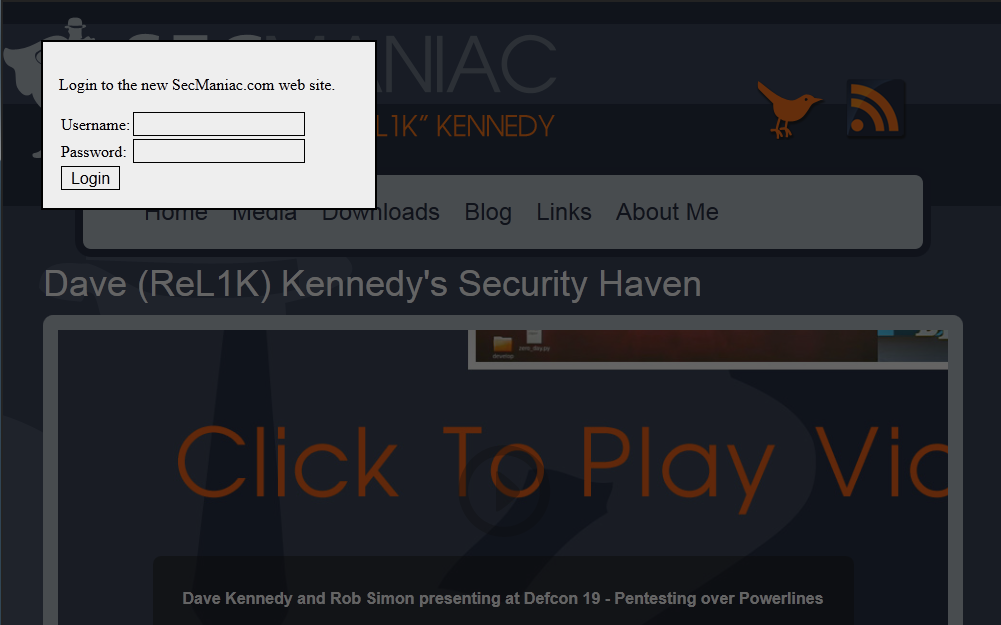
The credential harvester attack can use either a template built into SET, a cloned site, or a custom site stored on the SET machine. Typically, you would clone the client's site, which would include a login form. Since my client didn't have a login form on their site I decided I would need to make one. I created an index.html file that imports the victim site in an iframe and uses CSS to create a popup login box. I saved the file to my pentest machine and imported it into SET when prompted. The custom HTML file can be downloaded here.
To use the custom HTML file start SET, choose option option 1 for Social Engineering Attacks, then choose option 2 for Website Attack Vectors, then choose option 3 for Credential Harvester Attack Method. Next, choose to import a custom website by selecting option 3. You will be prompted to enter the path to the custom index.html file and the URL of the victim site you are impersonating. After that, SET will start up the web server and serve up your custom HTML file.
set:webattack>3
[-] Email harvester will allow you to utilize the clone
capabilities within SET
[-] to harvest credentials or parameters from a website as
well as place them into a report
[!] Example: /home/website/ (make sure you end with /)
[!] Also note that there MUST be an index.html in the
folder you point to.
set> Path to the website to be cloned:/path/to/index_html/
[-] Example: http://www.blah.com
set> URL of the website you imported:www.secmaniac.com
The best way to use this attack is if username and password
form fields are available. Regardless, this captures all
POSTs on a website.
[*] I have read the above message. [*]
Press {return} to continue.
[*] Social-Engineer Toolkit Credential Harvester Attack
[*] Credential Harvester is running on port 80
[*] Information will be displayed to you as it arrives below:
The attack page should look like this. If the victim enters their username and password, SET will record it and generate a report for you.