AverageSecurityGuy
Security, Programming, Pentesting
Password Cracking Server
by {"login"=>"averagesecurityguy", "email"=>"stephen@averagesecurityguy.info", "display_name"=>"averagesecurityguy", "first_name"=>"", "last_name"=>""}
I have been doing a lot of research into password cracking lately and have learned to use rcracki_mt, and the hashcat family of password crackers. One of the problems with password cracking is that some programs are better for certain types of hashes than others. For LM hashes I use rcracki_mt and the LM rainbow tables from freerainbowtables.com. These rainbow tables can break just about any LM hash. For other hash types like NTLM and Windows Domain Cached Credentials I find the hashcat family with some good word lists and rule sets work very well. It would be nice if there were one program that would accept a list of hashes and a hash type and would run the best program for the job.
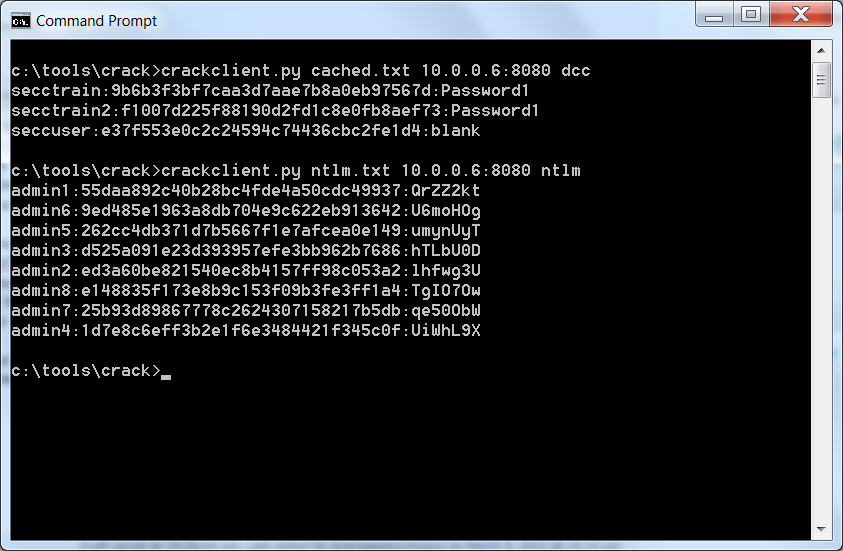
It seemed to me that this is the perfect time to write a script but I was not going to be satisfied with a glorified batch file. No, I wanted something cool. So I wrote a little Python module called crack.py. It defines two objects, a CrackManager and a CrackThread. The CrackManager reads a config file and loads a list of commands to run for each defined hash type. When CrackManager receives a password cracking request it creates a new CrackThread object that runs each of the commands in the config file. I then wrote a script called crackserver.py, which puts an XMLRPC server wrapper around the CrackManager class and allows me to submit password cracking requests over the network. I also wrote a script called crackclient.py that submits an XMLRPC request to the server and polls the server to determine when the cracking process is finished.
I plan to release a white paper soon but for now I have a couple of screenshots and you can download the code at github.
Crackserver.py
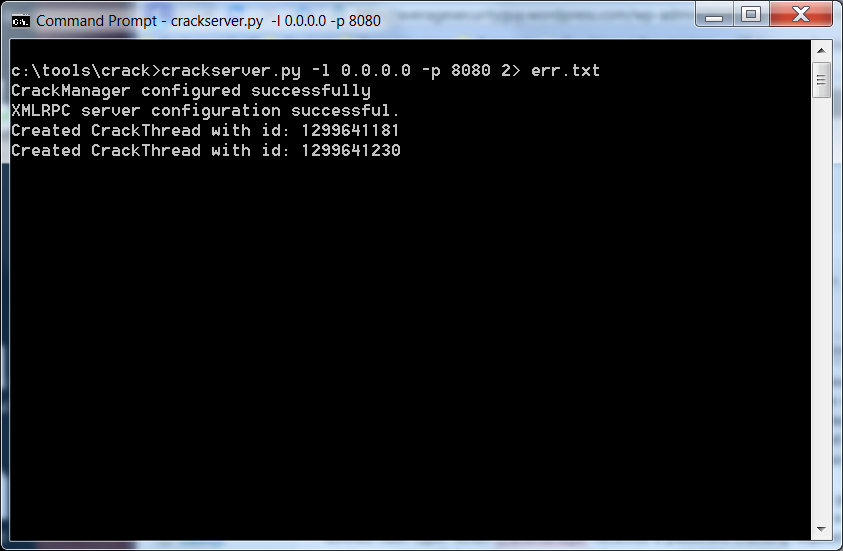
Crackclient.py